As cautious as some people are about their web browsing habits, they throw that caution to the wind when it comes to managing their passwords. This was apparent in a survey of some 1,000 Internet users performed for ComputerTrainingSchools.com by Op4G. Survey results found nearly two out of three people in the sample, 64 percent, said they practice so-called “safe web browsing practices,” while at the same time admitting they write their passwords down and use the same password across multiple sites, both critical security risks advised against by various cybersecurity experts and organizations.
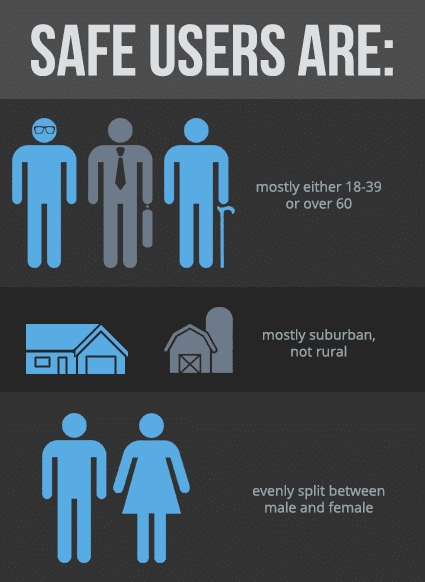
While looking at this “safe users” group, we discovered several demographic details:
- Most were either 18-39 or over 60
- Most were suburban residents as opposed to rural
- They’re evenly split between male and female
Additional drill downs on this group revealed some interesting – and somewhat contradictory – self reporting:
- 58 percent of safe users logged into social media multiple times a day
- 40 percent of female safe browsers were just as likely to share their passwords with life partners as to keep them private; an overwhelming 80 percent of male safe browsers were opposed to sharing passwords even with life partners
As defined by the survey parameters, safe users are people who have virus and malware protection on their computers, avoid sketchy websites, secure their home networks, craft strong passwords and don’t reuse passwords.
“Safe users'” Internet security blind spots and why they’re so bad
The results of the survey pinpoint two glaring problems in this group’s actual security practices — as defined by the users themselves – versus their perceptions of their relative security. We talked to a few cybersecurity industry experts to get their reactions and recommendations on these glaring problems.
Cybersecurity Sin #1: Writing passwords down
 Writing passwords down, in the opinion of many security experts, makes it easier for those passwords to be physically stolen or copied. The followup question to that dilemma? How are people protecting what they wrote the passwords on, if at all? Are they leaving a notebook full of passwords in plain sight near their computer when they’re not there, or is it locked in a drawer when its owner is away from their computer?
Writing passwords down, in the opinion of many security experts, makes it easier for those passwords to be physically stolen or copied. The followup question to that dilemma? How are people protecting what they wrote the passwords on, if at all? Are they leaving a notebook full of passwords in plain sight near their computer when they’re not there, or is it locked in a drawer when its owner is away from their computer?
John Fitzgerald, CTO of Wave Systems Corp., an endpoint data protection company, points out “writing” can mean different things to different people. “When they said they recorded a password, did they stick it into an Excel spreadsheet?” he said. “If they did, is it on a computer protected by anti-virus software or on one infected with a keylogger that’s stealing the passwords as they’re typed?”
“It’s never a great idea to write down your passwords and stick them under your keyboard, but there are worse ways to expose your passwords,” he added.
The convenience of writing down passwords can outweigh the risks in the minds of cautious Web users. “People feel more comfortable controlling the book because they know they can put it in a safe,” said Jon Rudolph, Sr., a software engineer with Core Security, a cyber-attack testing company.
The risk of loss or theft of a book of passwords can be easy to intuitively calculate by some people. “They know how often a book has been lost or stolen in the past so they have something concrete to compare it to,” Rudolph said.
“Whereas,” he continued, “some people are nervous about trusting their passwords to the cloud because they have no control or visibility into who’s looking at their password list.”
“Writing down the information isn’t the problem,” he added. “It’s how you protect the information after it’s written down.”
Of course the reason people write passwords down is they have too many of them to memorize. “Early on, people only needed a few passwords, but now we’re up to the hundreds for an individual,” Core’s Rudolph said. “It’s not feasible for an individual to remember all those passwords.”
Cybersecurity Sin #2: Sharing passwords

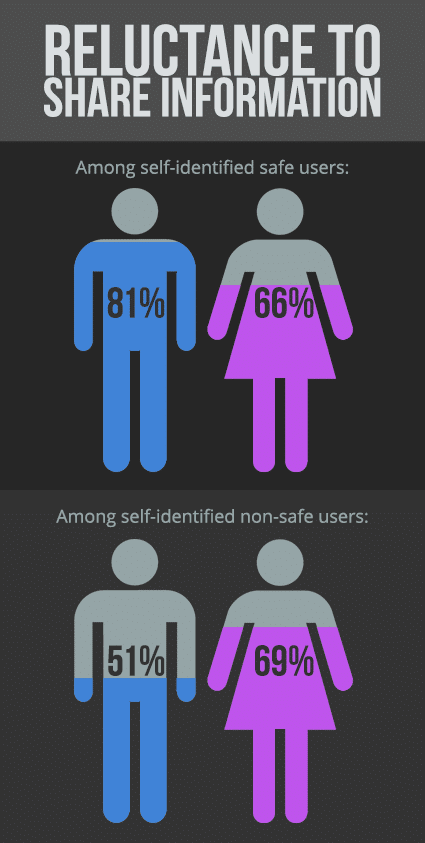
Sharing passwords is also practiced among self-proclaimed safe users in the survey, though there is a wide gulf between women and men on that subject. Two out of every five women (40 percent) said they were just as likely to share their passwords with their life partners as to keep them private. Four out of five men (80 percent), on the other hand, were against sharing passwords, even with life partners.
When it comes to sharing all one’s information with a life partner, men’s reluctance to do that remained about the same — 81 percent — while women against that practice jumped to 66 percent. That number climbs for women when non-safe surfers are added to the mix — 69 percent — but drops to 51 percent for men.
Tips for aspiring IT security experts
The reality that both standard users and network security managers have to face is that there’s no such thing as perfect security. Experience has shown virtually any software solution can be cracked or bypassed with enough time and effort. There’s no perfect escape from the specter of social engineering exploits either. People, fallible by nature, will make mistakes, and that includes doing all of the actions described above. Some cybersecurity experts acknowledge this, and advise those interested in moving into the IT security discipline to plan accordingly.
Security training and education still matters
Data security training and courses have the potential to be a major force multiplier for IT security managers, and beneficial in professional as well as personal use cases. The findings of this survey and similar ones would suggest there’s a degree of inconsistency in what people think “safe user” habits actually entail. Security training courses and security boot camps can help provide a common point of reference.
Prospective tech students and established IT pros looking to move into security-centric roles in particular can benefit from cybersecurity certifications. Some cert courses, like Cisco’s CCSP, focus on security training within a specific type of proprietary network infrastructure, while a cert like the CompTIA Security+ covers subjects like access control, cryptography and organizational security in a more vendor-neutral context.
Dealing with password recycling
Reusing passwords, another data security cardinal sin, may actually be inevitable. When the email addresses and passwords of approximately 1.3 million users across nine sites on the Gawker Media network were cracked in late 2010, an analysis of the leaked data by the University of Cambridge Computer Laboratory’s Security Group revealed that 76 percent of the victims reused passwords. A separate analysis from Microsoft developer and Web security specialist Troy Hunt compared the Gawker data set against the user data revealed in a later Sony PlayStation Network breach and found that, among users who had accounts on both networks, two thirds reused the same password.
“It’s simply unrealistic to think that an average user will create, record, remember and use a different complex password for each of the dozens of sites and accounts that they log in to daily,” said Scott Goldman, CEO of TextPower, an identity authentication system maker.
“Doctors want us to be perfect about our health care, trainers want us to be perfectly fit and mothers want us to have perfect manners,” he observed. “In reality, though, we do the best that we can given the circumstances of real life.”
A few experts offered potential strategies for both individuals to internalize, as well as security managers to integrate into the fabric their organization’s stated data security policies.
Rudolph of Core Security recommended that if passwords are reused, they be used with forethought. For example, reuse can be prioritized. Passwords for high-priority sites — like banks and email accounts — would never be reused, while those for lower-priority sites would be reused. “As long as you’re aware of what you’re doing, as long as you make your decisions with purpose, that’s a good strategy,” Rudolph said.
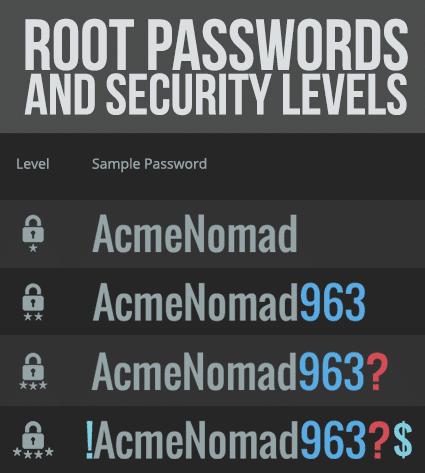
One password reuse approach suggested by Goldman is to create variations of a root password at various security strengths. For instance, such a root could be AcmeNomad. That would be used on relatively inconsequential websites. For a website where a slightly higher level of security is required, you could use AcmeNomad963. For a level-three site, you might want to use “AcmeNomad963?” and for highest security sites, “!AcmeNomad963?$.”
“So you’ve really only got one password to deal with and then remember the simple rules that go around it for various types of sites,” Goldman said.
Dealing with writing down and sharing passwords
One practical alternative to writing passwords comes down to web browsers. For example, some browsers have a feature for automatically saving passwords. Passwords can also be saved in a password manager either located on your computer or in the cloud. Those kinds of password managers usually use a single password to access all your passwords. That means one has to carefully protect that master password. Most people, though, just write it down, which sort of defeats the purpose of not writing down passwords in the first place.
As with scribbling down passwords, best practices dictate that user names and passwords not be shared. “I cannot think of one situation where sharing passwords is not a security risk,” CTO Fitzgerald said. “It may be fine and well-thought out today, but that could change 180 degrees tomorrow. At that point, you’ve given up the keys to your kingdom.”
“Even with something like two-factor authentication, if you give someone your phone and ask them to make a deposit to your bank account, you’ve essentially given someone your identity because that entity on the other end of the Internet has to believe it’s you,” he added.
Two-factor authentication requires you to have something you know — like a user name and password — and something you have — like a token or cell phone — before you can access an online account. Typically a short-lived code is sent via SMS message to a mobile handset that must be used before you’re allowed to log in.
While sharing credential information may create security challenges, the fact remains that our real world lives spill over into our digital lives. That may require a re-evaluation, on the part of IT security managers as well as standard users, of best practices. “Anyone that doesn’t share their passwords with their spouse, life partner or trusted relative is creating a nightmare scenario for the people they love if anything should happen to them,” said CEO Goldman.
“Imagine that you are incapable of logging into any accounts for a week — bank, utilities, investment, shopping, even password management accounts — and someone has to take over your digital/virtual life,” he explained. “If these sites and accounts can’t be accessed, not only is it impossible to conduct any daily activities or business transactions, but you’ve put your partner in a position of complete frustration dealing with something that will consume the vast majority of their time while they should be spending it taking care of you or your affairs.”
To men reluctant to share their credentials with their loved ones, Goldman has this advice: “Lighten up, men. Make sure your spouse/partner/significant other has a list somewhere. If the worst happens to you, you’ll be covered. If the worst happens to your relationship, you’ll need to just change some passwords. Which one sounds worse?
For people seeking careers in cybersecurity, the lesson is clear: Users and IT managers alike will need the right security education and training to overcome the kinds of security blind spots exposed in this survey.
Sources
Interview with John Fitzgerald, CTO,Wave Systems Corp. Interview conducted by John Mello, October 2014.
Interview with Jon Rudolph, Sr., Software Engineer, Core Security. Interview conducted by John Mello, October 2014.
Interview with Scott Goldman, CEO, TextPower. Interview conducted by John Mello, October 2014.
“Measuring password re-use empirically;” Light Blue Touchpaper, Security Research Computer Laboratory, University of Cambridge; February 9, 2011; https://www.lightbluetouchpaper.org/2011/02/09/measuring-password-re-use-empirically/
“A brief Sony password analysis,” Troyhunt.com, June 6, 2011, http://www.troyhunt.com/2011/06/brief-sony-password-analysis.html
